- Introduction
- What are Customer Chatbot Services and video Chatbots?
- Impact of Chatbot Customer Service on business
- Examples Of Conversational AI
- Conclusion
Being a good friend who replies late or ignores messages may not affect your identity much, but have you ever thought what if a business does the same? It can cost you a good amount of clients.
But now business has evolved a lot in this field with the introduction of Conversational AI, Chatbots and Virtual assistance. Which makes Artificial Intelligence Course a high opportunity field in today’s market. Conversational Chatbots have significantly reduced the time a business takes to respond to their customer. It has also changed the way businesses manage their internal processes.
Moreover, Conversational chatbots have taken a supreme position after the introduction of video chatbots, that use visual and audio technology to answer the queries of the customers. By leveraging AI, businesses are now able to maintain 24/7 customer support, streamline internal processes, and improve overall efficiency at a very low cost.
Let’s dig a little deeper to know how Conversational AI can improve customer and business service, and the benefits they put out to us.
What are Customer Chatbot Services and Video Chatbots?

Chatbot services are AI powered computer programs developed to mimic human interaction with the help of machine and data-based learning. These are programmed to extract answers from different articles and data present on the internet.
Besides commonly used Chatbots, the introduction of video chatbots have proved to be a massive hit. These chatbots work on audio linguistics technology and are capable of answering questions by taking audio instructions. The video graphic representation makes it more indulging and mimics real conversations perfectly.
Moreover, these services can be integrated in various platforms like websites, social media accounts or messaging apps like WhatsApp business and Instagram business profiles to make customer service convenient and accessible at any time. These chatbots are based on psychology for product management to work on self-improvisations and update themselves through client’s conversation and queries and provide more personalised assistance over time.
With a long list of benefits these chatbots have brought a big revolution for business customer services. Let’s see how.
Impact of Chatbot customer service on business
Chatbots have significantly received a warm welcome by the existing businesses and the employees. Let us explore how AI and conversational AI can improve customer and business service, and the benefits they bring to the table.
Round-the-clock support
One of the most significant benefits of conversational AI is its ability to provide round-the-clock customer service support. Customers can easily interact with chatbots to get answers to frequently asked questions, place orders, and resolve issues. This can save time for both customers and businesses, and improve overall customer satisfaction.
Additionally, chatbots can collect data and analyse customer behaviour, providing valuable insights for businesses to improve their products and services.
Streamlining Internal Processes with Virtual Assistants
Conversational AI can also be used to streamline internal processes and improve employee productivity.
For example, virtual assistants can help employees with tasks such as scheduling meetings, managing emails, and accessing important information.
This can save time and increase efficiency, allowing employees to focus on more strategic tasks.
Building Chatbots and Virtual Assistants
To build a conversational AI, individuals can pursue an artificial intelligence certification or take an artificial intelligence course. These courses can provide an understanding of the fundamentals of AI, machine learning, natural language processing, and more which can be useful for building chatbots and virtual assistants.
Additionally, there are several AI platforms available that make it easy to create and deploy chatbots without any coding experience. AI and Conversational chatbots have become so commonly used and hence is a vast growing opportunity field.
Let’s check how common they are and with how many conversational AI and Chatbots you are familiar with.
Popular Conversational AIs
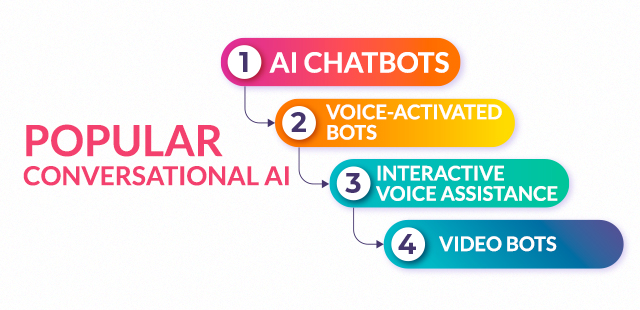
Conversational AI is no more about giving pre- built answers to questions asked in a certain language or manner but it has elevated itself in understanding commands in many commonly spoken languages and providing personalised responses.
There are mainly three types of conversational AI: –
AI chatbots: – These are most used chatbots in small businesses and e-commerce websites and social media and messaging apps popularly found in WhatsApp Business, Facebook, Instagram. These chatbots are very reliable for providing virtual customer assistance and are easy to install and use in your business.
Voice-activated Bots: – These bots use Interactive Voice Response technology which allows users to interact with computerised systems using voice command inputs or touch tone keypad inputs. They are mostly used to handle high volume of incoming calls and redirect it to the authorised person. Some popular examples are Ameliai and AVA.
Interactive voice assistance: – These are voice enabled devices which are programmed to mimic human conversations in many different and now even regional languages. They allow users to communicate in simple and generic language without giving any specific command.
Amazon Alexa, Google Assistant, Apple Siri, and Microsoft Cortana are most common and successful examples of Interactive Voice Assistance.
Video bots: – These chatbots use video content as means of communication instead of regular text based conversations. These are programmed on the basis of NLP which is Natural Language Processing and machine learning algorithms.
Most common and popular video bots are Meena by Google, Blender Bot by Facebook, Tay by Microsoft.
Conclusion

Conversational AI has a strong grasp in today’s market and hence has a great career opportunity.
If you have interest in this field and you want to pursue a course in Artificial Intelligence Course then go for upGrad campus online Artificial Intelligence certification course that provides you the complete package with Live Sessions, Mentor Support and Placement Assistance.